Chimera Ransomware Tries To Turn Malware Victims Into Cybercriminals

Ransomware is one of the most pernicious forms of malware with which your computer can be infected, and a new version of the malicious software is threatening to post all your files online while also tempting you to turn to the dark side and help spread the ransomware.
The Chimera ransomware -- named after the monstrous fire-breathing creature of Greek mythology -- was first spotted in the wild affecting customers in Germany. But researchers at security company Trend Micro recently uncovered a sinister new feature of the malware, which seeks to help accelerate its distribution by luring those affected into becoming carriers and infecting others.
Here we look at how Chimera works, why the criminals are trying to tempt victims into helping them, and what you can do to prevent your systems becoming infected.
What is Ransomware?
Ransomware is a type of malware that has become increasingly popular in the last three years. Once downloaded onto your system, this form of malware immediately begins to encrypt all your files and when you try to log on to your computer you are greeted with a ransom demand (typically paid for in bitcoins) which says if you don't pay, you will never see the files again.
Most ransomware normally comes with a message from a local law enforcement agency (FBI, Europol, National Crime Agency, among others) that says illegal material was found on your computer -- typically child pornography or pirated film, TV or music files. This is included to prevent the victim from reporting the incident to family, friends or the authorities.
While the people behind spreading ransomware are clearly criminals, they do typically unlock your files once you pay up. The reason being that if people thought their files were gone anyway, they would never submit.
How Is Chimera Ransomware Different?
The Chimera ransomware does everything other forms of the malware does, asking for 2.4 bitcoins ($865) to decrypt the files -- but it is different in two important ways: The first is that rather than simply threatening to leave your files encrypted and inaccessible forever, the operators of Chimera threaten to post all your files online. However, according to the Anti Botnet Advisory Center, there is no indication to date that anyone's details have been made public. Additionally, Trend Micro's research suggests "the malware has no capability of siphoning the victim’s files to a command-and-control (C&C) server."
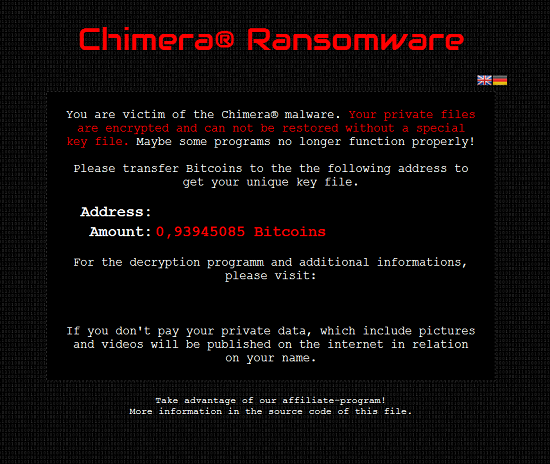
The second difference is even more sinister. A single line at the bottom of the ransom demand teases: "Take advantage of our affiliate program,” directing technically inclined victims to inspect the source code to find out more. In the source code is a Bitmessage address that lets you connect with the operators of Chimera for more information.
What Is Bitmessage?
Bitmessage is a decentralized, encrypted, peer-to-peer, trustless communications protocol that allows users to communicate anonymously. It is exactly the type of encrypted communication system governments are now threatening to outlaw in the wake of the ISIS terror attacks in Paris because they cannot monitor what happens on those channels. Indeed in the wake of Edward Snowden's revelations about the National Security Agency monitoring email communications, Bitmessage reported a big surge in users.
How Does The Affiliate Program Work?
The criminals behind Chimera will see the affiliate program as having a twofold benefit. The first is that if it gets other people to help spread the malware it will earn more money. Trend Micro said the criminals will take a commission of 50 percent on any ransom paid through the program. The second benefit is that using this method to spread the malware distances the criminals from the criminal act of infecting someone's computer and will make it even more difficult for them to be caught.
How Many People Have Been Affected By Chimera?
As with all ransomware, getting exact figures for Chimera victims is tough, but at the moment infections appear to be limited. In October it showed up being spread through false job applications or business offers in Germany, specifically targeting small or medium businesses whose data would be highly valuable.
Security researchers at Bleeping Computer and Emisoft told SC Magazine the Bitmessage address used to distribute the decryption keys had gone quiet by the end of November and while that could indicate Chimera is dead, it could just as easily suggest the operators had moved to use a different address or were readjusting the operation to avoid detection.
Are We Going To See More Of This?
Ransomware in the last three years, since the introduction of the Reventon ransomware in 2012, has grown in sophistication and popularity among criminals. Along with mobile ransomware, Ransomeware-as-a-Service (RaaS) is just the latest evolution of this type of malware and we are likely to see more of it.
"Peddling ransomware as a service (or RaaS) has some advantages. RaaS lessens the possibility of the illegal activity being traced back to the creators. Selling ransomware as a service allows creators to enjoy some profit without the increased risk of detection. For Chimera, the commission is 50 percent, a large payoff for lesser effort," Trend Micro researcher Anthony Joe Melgarejo said.
However Melgarejo pointed out that compared to other forms of ransomware (CryptoWall, TeslaCrypt) Chimera is not as sophisticated, and those who operate it may be leaving themselves open to identification. However, according to Trend Micro's own security predictions, 2016 will be "the year of online extortion."
How Do I Stop Getting Infected With Ransomware?
Once you have been infected, removing ransomware is typically impossible, especially if it has been properly implemented. Protecting yourself from installing the malware in the first place is relatively easy, however. Chimera was spread through spear-phishing emails designed to look like they come from reliable sources. In this case the emails contained a link to a Dropbox account, which, once clicked, sees the ransomware installed automatically.
As well as not clicking on suspicious links in emails or downloading suspicious files from unknown contacts, users can also back up their files externally regularly so should ransomware get installed on your system, you will be able to restore most of your files without having to pay up. For businesses, Trend Micro recommends keeping at least three copies, in two different formats, with one of those copies off-site.
© Copyright IBTimes 2024. All rights reserved.






















