As Hackers Increasingly Target The Cloud, Rackspace Turns To Military Vet With Cyberwar Experience

LONDON -- In the dead of night, two Navy SEALs and a former military officer glide toward a U.S. military facility, water lapping quietly against the side of their canoe. Suddenly two navy boats gun their motors as they pass the trio, but they fail to spot the group attempting to break into the secure facility.
This is the kind of operation the former officer, Brian Kelly, handled for a few years as a special ops consultant for the U.S. government, to identify gaps in security. (In fact, no one spotted him that night in 2014, and he was able to penetrate the facility, resulting in the firing of a soldier found asleep on the job.) The skill set landed him just a few months later at cloud computing company Rackspace as its chief security officer, using his stealth and smarts to protect the data of the firm's 300,000 customers.
Now he's facing unprecedented attacks on an entirely new battlefront: the cloud.
A recent report says 87 percent of organizations are making use of cloud infrastructure while research firm IDC is predicting cloud infrastructure spending will rise to more than $33 billion in 2015, accounting for a third of all information technology spending. As evidenced by the Dell-EMC megamerger this week, the future of computing is in the cloud, and everyone knows it -- especially the hackers.
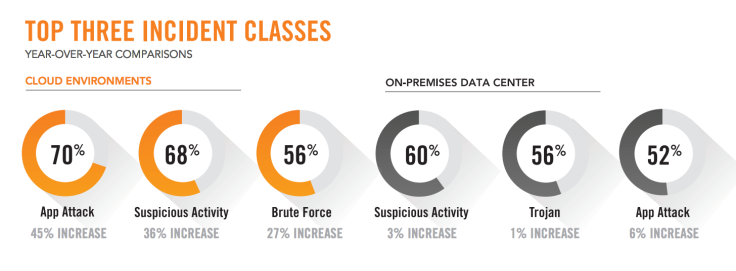
According to Alert Logic’s Cloud Security Report 2015, cyberattacks against cloud systems increased by as much as 45 percent in 2014 while attacks against on-premises infrastructure remained flat. With the huge rise in cloud adoption, together with the ever-decreasing cost of deploying applications and services in the cloud -- Amazon alone has dropped the prices of its Amazon Web Services offering nearly 50 times since 2006 -- hackers now have a much larger surface to probe for access to sensitive data.
Turn The Tide
To take on hacking groups that are well resourced and highly sophisticated, Kelly relies on his military training to turn the tide in favor of the good guys.
He describes his efforts to secure Rackspace’s network as “defending the homeland” and has organized the company in a military fashion, following the principle of unity of command, which Kelly said can be transferred directly from the physical battlefield to cyberspace when an attack takes place: “Within a company it needs to be very clear who the incident commander is, and all the other executives have to understand that they have to stand down and trust that the incident commander is going to lead them through this incident.”
This is a theory Kelly tries to get his customers to adopt, but it is also something he implements rigorously at Rackspace. He will take the reins if a security breach is deemed a tier two attack, but if a tier one attack is detected, which could do serious reputational or financial damage, Kelly knows he has to step aside and let Chief Operating Officer Mark Roenigk take charge.
With such unprecedented levels of cyberattacks taking place against cloud infrastructure, Kelly said he's regularly asked if cloud storage of data is safer: “I don’t think it’s a black-and-white answer, but I think with the exception of those small percentage of companies that can invest and do all the things they can do, cloud is a better bet.” Kelly admitted he has a “slight bias,” considering his current position.

Uneven Handshake
When Kelly joined Rackspace a year ago, he saw a major issue with the way cloud companies dealt with customers. He saw a situation where cloud providers took little to no responsibility for protecting the data once the customers had signed up for their services, a relationship he dubbed the “uneven handshake” and something he was not comfortable with.
“It is time that we even out the handshake, that cloud providers do more,” Kelly said. “Given our access, given our scale, given the depth of resources we have there is a lot more we can do.” At his first meeting with the board of directors of Rackspace he was equally blunt, telling them he won't be able to prevent attacks from taking place, but he could work to make detecting the attacks much better.
To do this, Kelly once again looked to his military past. In the 1980s, the U.S. government created three cybersquadrons -- offensive, defensive and research/hunting -- and when it came to filling out his operational security team, Kelly interviewed the original three commanders of these squadrons as they had "operational experience and operational discipline" and hired two of them.
Kelly is bringing some of that military operational discipline to Rackspace, carrying out multiple hunting missions within the company to make sure attacks don't come from within.
"A Waste Of Time And Money"
From his customers point of view, the challenge is to provide adequate security to companies who simply don't have the resources to protect themselves against the scale and sophistication of attacks we see today.
To date, these smaller companies have been left to fend for themselves, and, as Kelly sees it, they are wasting their time: “They get some quasi-security technology guy and he goes out picks a handful of products, plugs them in and we know that with the nature of the threat today, it is completely useless. A waste of time and money. Anyone who is targeting them is going to be in without any issue at all.”
While taking more responsibility and using Rackspace's security resources may reduce the risk significantly for its customers, it is not going to deter the more sophisticated and well-resourced hacker groups from continuing to attack the cloud.
Information Sharing
To address that, the industry needs to make a change, and Kelly is leading the charge to make sure this happens by once again looking to his past.
The original Information Sharing and Analysis Centers were established to help share information on cyberthreats to critical infrastructure, but as Kelly knew from his involvement, their success was limited due to the slow pace of information sharing. However the military veteran knew the potential to make a real difference if they managed to make efficient information sharing a reality.
With Kelly leading the charge, the Cloud Security Alliance (CSA), which counts among its membership all the main players in the cloud computing world, has established an information sharing platform to allow companies to share data anonymously about breaches to prevent hackers from using the same methods to attack one company after another.
“I think security professionals understand the value of information sharing. Unfortunately as an industry, we haven’t been very successful of that,” Kelly said. The new system, known as Cloud Cyber Information Sharing Center, is hosted at Rackspace and is just getting up and running, but Kelly said he hopes it will disrupt the operations of the groups he sees attacking his customers' data everyday.
“The key discriminator is that we are trying to exchange information at a very tactical level and we are trying to exchange that information in a matter of minutes if not hours. If I see an attack tonight, I will have my operational team characterize that attack in as much detail as possible, and get that on the wire as quickly as possible and into the hands of Microsoft and Google and Amazon and Dropbox.”
Driving Up The Costs

In recent weeks there has been the high-profile visit of Chinese President Xi Jinping to the U.S. and declarations by President Barack Obama that sanctions would be imposed on any Chinese companies found to be stealing intellectual property from U.S. companies. Since the deal was struck between Jinping and Obama, the Chinese government last week arrested five hackers at the behest of the U.S.
For Kelly, it’s all about driving up the costs of being a hacker and by using this approach, the industry has been successful at squeezing out the small players and nonprofessionals. While this means fewer groups attacking, it also means more room for the big guys to attack, groups including organized crime and nation states.
By sharing information in a fast and effective manner, Kelly and the CSA are hoping to drive up the costs of attacking the cloud for these groups too, particularly when it comes to the use of expensive tools known as zero-days, which are previously unknown vulnerabilities in software and which are sold for a lot of money on the dark Web.
“If I see a zero day, of course I am going to have to deal with it at the time, but as quickly as humanly possible, I am going to get that out to my peers with the hope that the rest of the cloud providers are going to know about it, and when [the hackers] try and go to one of them, it is not going to work. Now we have driven up their costs.”
The cat-and-mouse game of cyberattack versus cybersecurity is a constantly evolving environment, and just as hackers have adapted from targeting PCs to targeting smartphones, they are now looking to the cloud as the next big target. Companies need to know exactly what their responsibilities are, but just as important is the need for cloud providers to meet them halfway.
© Copyright IBTimes 2024. All rights reserved.






















