How To Stop Ransomware, The Cyberattack That Holds Your Computer Hostage Until You Pay
Russian hackers are bringing a whole new meaning to “disruptive.” Hackers from Eastern Europe and rural areas of Russia are increasingly targeting Western Internet users with so-called ransomware, malicious software that locks users out of their own computers until they agree to pay a fee -- typically thousands of dollars.
The FBI and cybersecurity researchers have issued increasingly urgent warnings over the course of 2015, culminating this week with a list of the best ways to avoid becoming a victim. While attack details vary, cases typically involve a user opening his or her computer to find a note saying all the machine’s files – family photos, financial documents, music, anything of value – have been encrypted, and the only way to unlock the system is to pay a bitcoin ransom within a certain time window.
All it takes is for a victim to click on an infected advertisement, email link or, most commonly, download a disguised email attachment (known as a Trojan).
“It’s still a relatively new form of cybercrime, but it’s becoming one of the most popular criminal business models, and that’s because it works,” said Stu Sjourwerman, founder and CEO of the security company KnowBe4, adding that between 5 and 10 percent of those affected will generally pay the ransom. “There’s no good way to get rid of it if you’re infected.”
Chatter on Reddit and social media included comments from users who reported finding malicious ransomware ads on Kickass Torrents before Google blocked the piracy site for failing to remove malware.

Cryptoviral extortion, the technical name for ransomware, has been around in some form since 2005, when a number of Russians were hit with a virus that permanently displayed a pornographic image on their computer unless they paid to have it removed. The money-making scheme has exploded in popularity since the rise of bitcoin, a form of digital currency that’s extremely difficult to trace.
Avoiding Ransomware
The best way to avoid it, the FBI says, is to always backup a computer’s contents on an outside device. If all that sensitive information is on an external hard drive that can mitigate the loss. Unfortunately, there's no certain way to stay safe, but Internet users are also encouraged to use ad-blocking software, or browser filters that will prevent malicious ads from ever appearing in the first place.
But as attacks become more frequent, counterattacks are ramping up. The cybersecurity companies FireEye and Fox-IT previously worked together to create decryptcrpytolocker.com, a free service that promised to unlock files encrypted as part of the CryptoLocker ransomware campaign. It’s conceivable that more of these services will surface as strains of ransomware become more prevalent.
The FBI also asks that any Internet user caught in a ransomware trap report the incident to the Internet Crime Complaint Center.
The most significant strain of ransomware is known as CryptoWall, which cost victims at least $18 million between April 2014 and June 2015, according to the FBI, with each shakedown demanding between $200 and $10,000. If a victim fails to meet that window the demand often doubles, or triples. That’s not including the additional costs procured by legal fees, credit monitoring and additional protections.
A Maine police department had its data and files taken hostage in April. In this case the police agreed to pay a $300 fee, though a Symantec report that tracked 5,700 ransomware attacks found that three percent of those affected paid the fee.

Businesses are increasingly becoming a target, both because they need the information and can afford to unlock it. A new ransomware strain just discovered this week targets Terminal Services, for example.
“We’ve seen a huge uptick in the last 60 days,” Lance Mueller, a senior incident response analyst with IBM’s Emergency Responses Services team, told USA Today in June. “We used to get 10 to 12 calls a month, in the last 60 days we’re getting that many in a week.”
Going Mobile
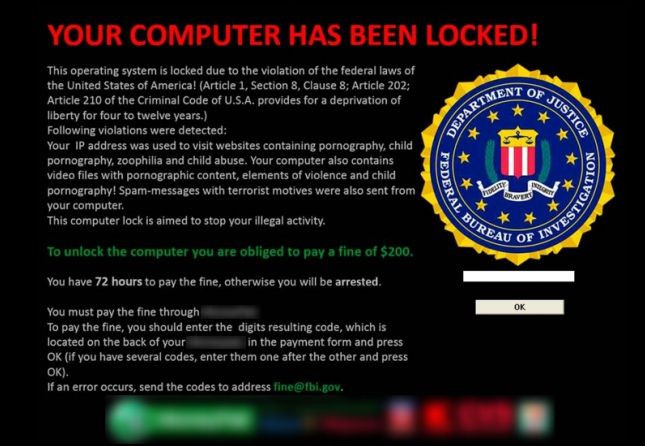
And now it’s going mobile. The security company ESET went public last month with Porn Droid, a form of ransomware disguised as an Android pornography app that almost exclusively targeted U.S. smartphone owners. Once installed, the app triggered a warning that appeared to be from the FBI, saying the phone accessed forbidden websites and that it would be locked forever unless the owner paid $500 within three days.
ESET suggested that the ransomware originated in Russia or Eastern Europe, often cited as the area of origin for this kind of attack. Young people, particularly in the rural areas of Russia or Ukraine, often leave school with exemplary skills in math and science only to graduate into a world of unemployment or low-paying jobs. Cybercrime has thrived in these areas, often in cubicle-lined offices, with top hacking groups believed to carry out attacks on the West with at least implicit permission from the Federal Security Service.
The hackers who designed the point-of-sale malware that compromised 40 million credit card numbers in the 2013 Target data breach were two Russian men, ages 17 and 23, after all.
© Copyright IBTimes 2025. All rights reserved.




















