MacOS 10.13 High Sierra Update: Security Bug Allows Settings Changes Without Password
Apple is once again dealing with password-related problems as a flaw in the company’s MacOS 10.13 High Sierra operating system appears to contain a security flaw that settings to be changed without entering a password.
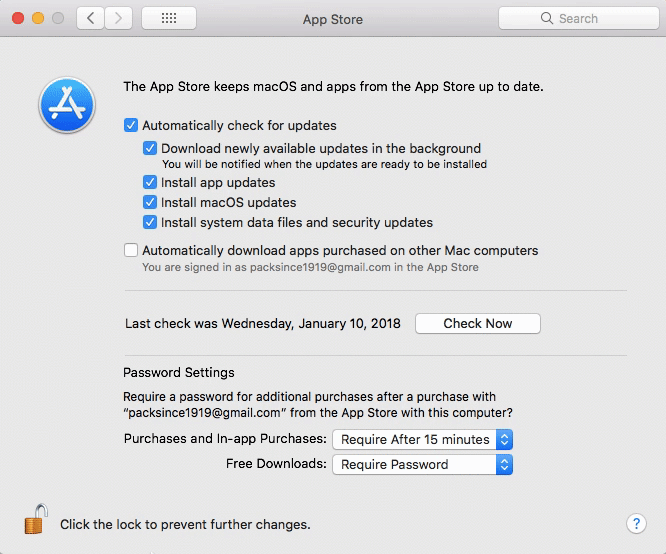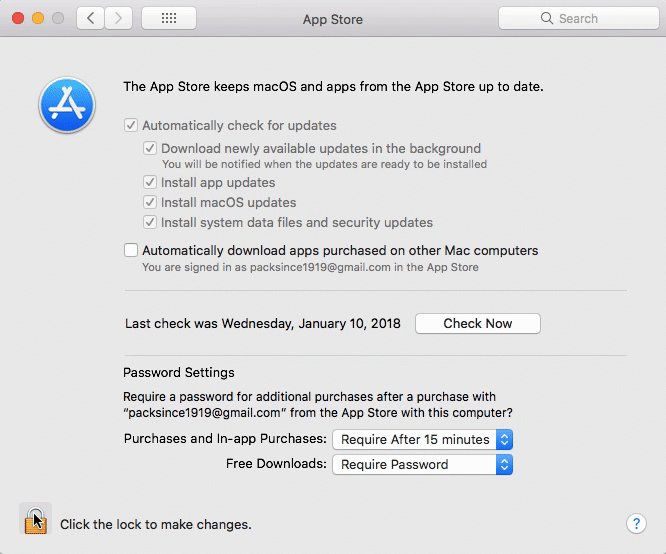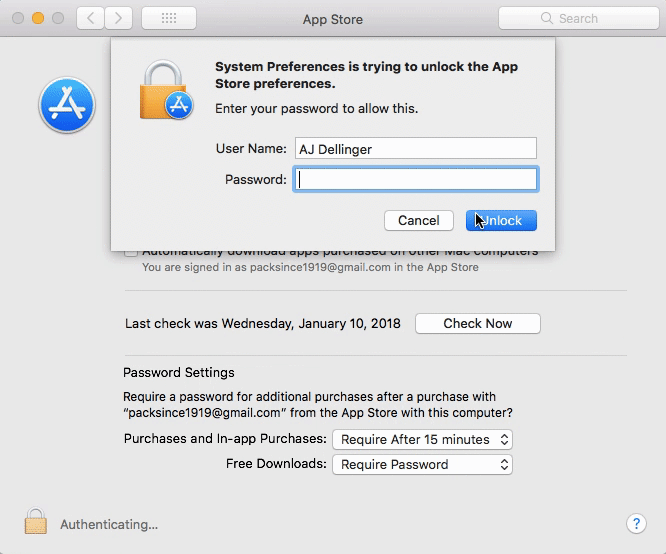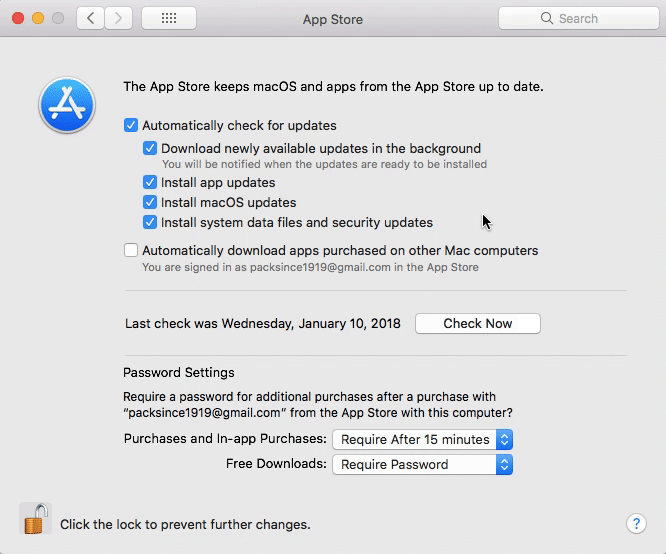
The bug, first reported on community reported bug service OpenRadar, allows an already logged in user with administrative powers to make changes to account preferences in the App Store to be modified without requiring the user enter a password for verification purposes.
Perhaps the strangest and most troubling part of the bug is the fact that it does prompt the user to login as is typically required any time settings are changed within the operating system—but it doesn’t matter if the user actually enters the password.
Leaving the password text box blank or entering literally anything—including an incorrect password—will still allow the user to perform the changes to the account’s App Store preferences.
International Business Times was able to replicate the issue on a MacBook Air running macOS 10.13.2.
The password issue will without question require a fix; it’s unacceptable that a login prompt can be bypassed by simply ignoring it or entering incorrect information. However, as far as potential security flaws go, the potential for attack is somewhat limited.
First, an attacker would need to have physical access to the device itself and either have the administrator’s password (which would allow them to make changes to the system even if the login requirement worked properly) or gain access while an administrator is already logged in.
Assuming the attacker would be able to gain such access, they would still only be able to change the user’s preferences in the App Store. That includes options for automatically downloading and installing updates and, ironically, modifying how often the App Store should require a user to provide their password for purchases and downloads.
While those settings leave limited options for malicious activity, a threat actor could set up additional attacks by preventing the machine from automatically downloading and installing necessary updates, including those that patch security flaws. That would leave those flaws exploitable on the machine.
Thus far, it doesn’t not appear that the password bug in the App Store is present anywhere else within macOS 10.13 High Sierra. Apple did not respond to request for comment regarding the security flaw.
The issue is the second high-profile, password-related security flaw to strike Apple’s popular operating system in recent months. In November, a similar bug was discovered that allowed anyone to gain administrative access to the machine without entering a password.
In that instance, the threat was much more severe, as it didn’t require a user already be logged in to gain administrative access. The bug could be exploited at the login screen or from within the system itself. Apple quickly issued a security fix for the issue.
© Copyright IBTimes 2024. All rights reserved.





















