Porn Droid Android App Revealed As LockerPIN Ransomware Locking Your Smartphone

Russian hackers are spreading a piece of Android malware disguised as a pornography app and are targeting users in the U.S., demanding a ransom of $500 to unlock your phone.
The hackers are using social engineering -- customizing emails and social media messages to target specific individuals -- to spread the app, known as Porn Droid, aimed almost entirely at users in the U.S. When installed on an Android smartphone, the app silently downloads a piece of malware called LockerPIN, which resets the screen-lock PIN and effectively locks the user out of his/her smartphone.
Like all ransomware, the app displays a warning claiming to come from an official source -- in this case, the FBI, telling victims that information about their location and snapshots of their face have been uploaded to the FBI cybercrime datacenter. The warning says that forbidden pornographic sites have been accessed on the victim's phone.

This is typical for ransomware demands, but the use of the FBI in the warning message shows that the hackers are targeting victims in the U.S. specifically.
And the effects are worse than with typical ransomware: Even if users pay the ransom, they still don’t get access to their smartphone, because the LockerPIN malware randomly resets the PIN code, so not even the hackers behind this campaign know the code.
Hundreds Already Infected
According to security company ESET, which uncovered the campaign, the only way to recover access to your phone is through a factory reset, which means that all your photos, videos and contacts will be deleted and, unless they have been backed up, will be lost forever.
ESET says that while the Porn Droid app is not available through the Google Play store - thereby limiting infections — it has already detected a few hundred users in the U.S. having being infected with the LockerPIN malware.
The Porn Droid app is being distributed through warez forums, torrent sites and third-party app stores, and ESET says the hackers are also using social engineering tactics to help distribute the app.
Asked where the Porn Droid malware originated, Lukas Stefanko, malware researcher at ESET, said it came from Russia, adding the caveat: “We are not 100 percent sure, but there are a few indicators that suggest this malware might have origins in Russia. But we cannot claim that with certainty.”
Last week it was revealed that another app claiming to be a pornography app -- Adult Player -- took pictures of users before demanding a ransom from them.
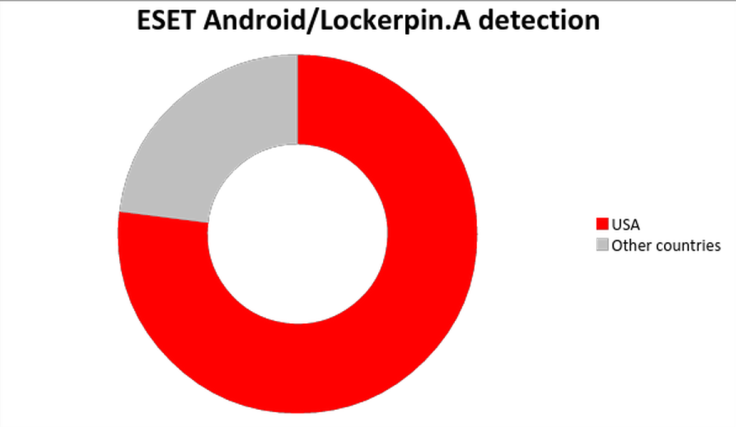
ESET’s LiveGrid statistics show that 75 percent of all infections are located in the U.S. with ESET, saying “this is part of a trend where Android malware writers are shifting from mostly targeting Russian and Ukrainian users to largely targeting victims in America, where arguably they can make bigger profits.”
Speaking about the findings, Kevin Epstein, from security company Proofpoint, says that the hackers are exploiting the weakest link in any security chain -- humans. “The social engineering component of this attack, wherein devices are compromised because a user allows the malware administrative rights, suggests mobile users are just as vulnerable as laptop users. The solution: Don’t click on anything that you don’t understand.”
© Copyright IBTimes 2025. All rights reserved.




















