Syrian Refugees Hoping For US Resettlement Face Gauntlet Of Interviews, Collection Of Biometric Data
Multiple interviews conducted over a span of years and by different agencies are the primary method of identifying potential security threats.
Anonymous' ISIS Operation Twitter Lists Are 'Wildly Inaccurate' And Causing Headaches At Twitter
Thousands of the supposedly ISIS-affiliated accounts submitted to Twitter aren't ISIS-affiliated at all.
John Bel Edwards, Pro-Gun Democrat, Wins Louisiana Governor's Race Over Sen. David Vitter
John Bel Edwards, who is pro-gun and anti-abortion, is the first Democrat to be elected governor in the Deep South since former Gov. Kathleen Blanco left office in 2008.
Massive Blackout In Crimea After Transmission Towers 'Blown Up' By Unknown Parties
Russian media reported that saboteurs knocked out power lines, nearly two years after Russia annexed Crimea.
Russian CyberBerkut Hackers Link ISIS To Ukrainian Weapons Negotiations With Qatar: Russian Media
The allegations, surfaced by state-controlled Russian media, don't conclusively prove that Ukrainian weapons made it into the hands of the Islamic State group.
Black Friday 2015 Headphone Sales: Beats, Sony Bass Have Big Discounts, But HiFiMAN Slashed Prices By $200
Turkey always tastes better when you can drown out family members with a thumping bass.
Donald Trump Supports Syrian Database, Promises To Send Refugees Back If Elected
Trump also promised to employ surveillance against mosques in the U.S.
Leaked Downloads of Adele's New Album '25' Fill Kickass Torrents, The Pirate Bay
Studies have consistently shown that making popular music available on streaming services reduces illegal downloads.
NSA Email Collection Continued Mapping Social Connections Between Americans, Foreigners Past 2011
Changes authorized NSA analysts to inspect American messages sent overseas with less judicial oversight.
EU Targets Bitcoin, Anonymous Currency In Fight Against Terrorist Financing
Bitcoin is the most popular form of digital cryptocurrency, with users able to transact in relative anonymity.
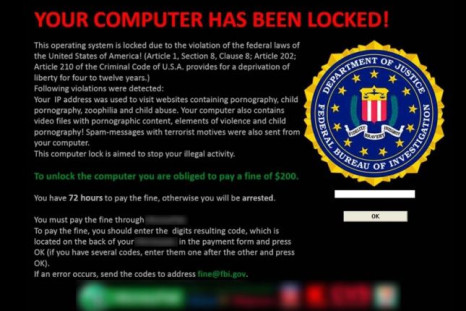
Ransomware Hackers Will Start Holding Medical Devices Hostage In 2016: Research Report
The healthcare industry is already breached more often than any other, and ransomware is sophisticated enough to stump the FBI.
Telegram Just Deleted 78 ISIS Channels From Secret Chat App Amid Encryption Scrutiny
It's a big change for the app, which previously only removed spam as part of its terms of service.
DDoS Attacks Will Continue Smacking Video Games, Email Providers, And It's Not Just Lizard Squad
One video game company is hit with 30-40 DDoS attacks every day from angry gamers who pay a small fee to have the service disrupted.
Who Needs YIFY Movies? Popcorn Time Torrent Downloads Return, Hoping To Avoid MPAA Pressure
Users will need to uninstall any existing version of Popcorn Time, download VPN.ht Movies and hope the MPAA doesn't bring it down.
UK Admits Developing Cyber Weapons To Attack ISIS, Hackers
British spies are currently monitoring 450 cyberthreats against companies, the U.K. finance minister said at a meeting Tuesday.
Police Body Cameras Infected With Conficker, A Notorious Computer Worm
The worm previously targeted French, German and British military computers.
ISIS Hackers Love To Threaten The US, But Don't Expect Them To Turn Off the Lights Quite Yet
Despite ISIS' claims of advanced cyberskills, it would likely take a state-sponsored hack to infiltrate the most critical infrastructures in the U.S., tech analysts say.
Demonii Torrent Tracker Down: YIFY Movie Group Pulls Demonoid Tribute Offline After MPAA Trouble
It's another hit for the piracy community, which has watched as YIFY, Popcorn Time and others have disappeared.
Video Shows SpaceX's SuperDraco Rocket Thrusters, Designed To Help Astronauts Avoid Catastrophe, In Action
The SuperDraco will provide 200 times more power than its predecessor and is designed to help a Dragon crew abort a mission and land safely.
Silk Road Bitcoin Auction Complete: Four Bidders Take Home $14.3 Million In Digital Currency
One of the main motivating factors behind the Silk Road was spreading libertarian ideals.
How Private Torrent Trackers Work: Inside The Next Exclusive, Invite-Only World Of Illegal Downloading
"Access to this website is a privilege, not a right, and it can be taken away from you for any reason,” warn the rules on one private tracker.
FBI Paid $1 Million To Break Tor Anonymity As Part Of Silk Road 2 Investigation, Tor Says
The accusation comes after widespread suspicion over a canceled presentation at the 2014 Black Hat conference.
Google Play Apps Seek 253 Permissions On Android Phones, Poll Finds, And They Better Be Honest About It
Nine-in-ten Google Play Store users said its “very” or “somewhat” important to have clear information about how an app will use their data.
Change Your Comcast Password: 590K Account Credentials For Sale For $1,000 On Dark Net
The company was responding to a dark net sale that offered 590,000 user credentials for $1,000.
Obama's Facebook Cover Photo Shows Climate Change A Top Priority For White House
Six months after POTUS joined Twitter he's now on Facebook to get people talking about climate change.
Cryptowall 4 Is In The Wild, After Previous Versions Extorted $325 Million From Ransomware Victims
Watch out for this malware by avoiding phishing emails or by backing up your hard drive.
MyFreeCams.com, Popular Adult Site, May Put Models At Risk With Weak Passwords
MyFreeCams.com hovers among the most popular 1,000 websites online, even with bad security practices
Ku Klux Klan Calls Anonymous List ‘Pathetic,’ Civil Rights Groups Agree
Most names of alleged Ku Klux Klan members revealed on Pastebin by a hacktivist group are said to be already well-known to authorities.
ProtonMail, Encrypted Email From 'Mr. Robot,' Downed By DDoS Even After Paying Ransom
ProtonMail joins Runbox and VFEMail as the encrypted email services forced offline this week.
Insurance Companies Are Treating Hackers Like Natural Disasters, And That's Good For Your Personal Data.
Top insurance carriers are hiring companies that can predict the fallout from a data breach, just like they do with natural disasters.