Researchers Discover Hackers Can Hide Malicious Software In Subtitle Files

Researchers have discovered an exploit that uses subtitle files to take control of users’s devices. The flaw can easily be exploited on various media players including VLC, Kodi, Popcorn Time and Stremio.
“By crafting malicious subtitle files, which are then downloaded by a victim’s media player, attackers can take complete control over any type of device via vulnerabilities found in many popular streaming platforms,” researchers at Check Point Software Technologies said in a report. “We estimate there are approximately 200 million video players and streamers that currently run the vulnerable software, making this one of the most widespread, easily accessed and zero-resistance vulnerability reported in recent years.”
The Check Point researchers also said that the vulnerability can be exploited regardless on what device a victim is using, whether it’s a PC, smart TV or even a mobile device. Attackers could easily sneak a malicious file alongside the subtitle file. This has caused major concern as subtitles are downloaded from trusted repositories by many media player apps.
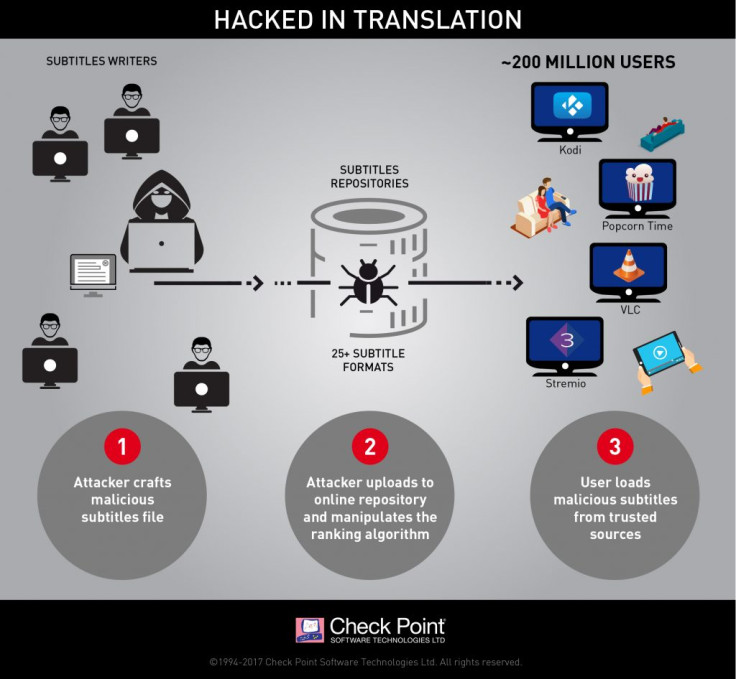
There are currently over 25 subtitle formats, and each format comes with unique sets of features and capabilities. This why a lot of media player apps parse together multiple subtitle formats to ensure coverage. The problem with this is that these media player apps might be downloading malicious files that have been placed there by attackers.
“By conducting attacks through subtitles, hackers can take complete control over any device running them. From this point on, the attacker can do whatever he wants with the victim’s machine,” Check Point researchers said. “The potential damage the attacker can inflict is endless, ranging anywhere from stealing sensitive information, installing ransomware, mass Denial of Service attacks, and much more.”
Although this newly discovered vulnerability could affect millions of users worldwide, some media players have updated their software to defend against this kind of attack. Popcorn Time, Kodi, VLC and Stremio have all officially released software updates that fixes this issue.
There’s no word yet as of this writing on whether other media players have addressed and fixed the issue. It’s probably best for users to stay away from using other media player apps that have not been updated to defend against this kind of attack, as pointed out by Engadget.
Some media player apps can automatically download subtitle files from major repositories like OpenSubtitles.org, which can offer hackers an easy portal to initiate this kind of attack. Check Point also shared a proof of concept video demonstrating how the exploit works.
Disney’s “Frozen” is played on Popcorn Time that’s running on a Windows PC. When adding an english subtitle, it can be seen on the right side that the attacker, using a Linux computer, now has full control over the victim’s PC.
Aside from the details shared above and the demonstration video, Check Point didn’t disclose any additional information about this exploit. The research firm says that it didn’t publish any further technical details so that developers have more time to address the issue.
© Copyright IBTimes 2024. All rights reserved.




















