There have been a lot of talks regarding the involvement of the United States and Israel behind a Stuxnet cyber attack, but with no concrete evidence to confirm the same. However, a latest report tends to claim that the US has indeed played a crucial role in that matter.
According to experts, the virus is so complex it could have only been created by a nation state - leading to speculation it was launched by the United States or Israel to damage or spy on the region's governments.
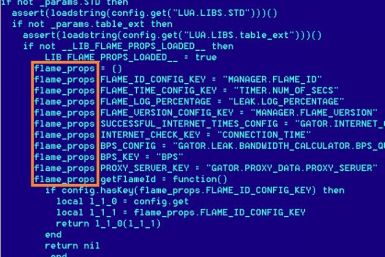
Researchers at the Russian security firm Karpersky have discovered a new highly sophisticated malicious program that has been used as a cyber weapon to collect private data from thousands of computers in Middle East countries like Iran and Israel and also in North Africa.
Members of the hacktivist collective called Anonymous lashed out at the International Police Association http://ipa-iac.org (IPA) on Friday afternoon. The Anonymous hackers responsible left an angry message on the website's homepage, stating that they defaced the page for the lulz (for fun) but also warned that they might have stolen some sensitive data.
What is CISPA? This article breaks down the bill that has Internet privacy advocates concerned that it would end the Internet as we know it.
CISPA sponsors are realizing the bill is a major threat to Internet privacy akin to SOPA, apparently in response to a groundswell of opposition from across the world.
You may not be able to see or hear it, but new research has found that one in five Mac computers carry Windows or Mac Malware.
Internet and network security provider Check Point Software Technologies said it expected to meet second-quarter estimates, after reporting a rise in first-quarter net profit that beat forecasts on strong sales of its new products.
Enraged hackers broke into the websites of drugmakers that produced pills tainted with poisons, in an attack against what they called the failure of Chinese societyi to protect citizens.
Last year, representatives from the State Department and the Pentagon took part in two exercises with their Chinese counterparts where they had to describe what they would do if it emerged the other side was behind the release of a sophisticated computer virus damaging national assets.
Facebook has signed on in support of the Cyber Intelligence sharing and Protection Act (CISPA), a controversial new Internet privacy bill would make it easier for government intelligence agencies and private firms to exchange information regarding potential and emerging cyber-security threats.
The Pentagon is establishing a fast-track acquisition process that would enable it to develop new cyber warfare capabilities within days or months if urgently needed, the Defense Department said in a report to Congress.
This article teaches you how to fight against CISPA, the online spying bill currently before Congress.
As many as 600,000 Macs worldwide have been infested by the sudden attack of Flashback Trojan.
The cybersecurity community raked Apple Inc over the coals on Wednesday, saying the company had dragged its heels on eradicating malware that experts say may have infected up to 600,000 Macintosh computers and can be used to ferret out sensitive user information.
A global cyber arms race is engulfing the Internet and the best way to counter the rapidly escalating threat is combining the efforts of U.S. agencies, private firms and international allies, cyber security officials said on Tuesday.
The U.S. House of Representatives will take up a cybersecurity bill at the end of April that lets the government and corporations share information about hacking attacks on U.S. networks, with amendments intended to ease civil liberties concerns, lawmakers said on Tuesday.
Is CISPA the new SOPA? This article decodes the Cyber Intelligence Sharing and Protection Act, the scariest threat to Internet freedom and privacy currently before the U.S. Congress.
The activist hacker group Anonymous plans to launch further attacks on Chinese government websites in a bid to uncover corruption and lobby for human rights, a member of the group said on Monday.
Accused LulzSec hacker Cody Kretsinger pleaded guilty on Thursday in federal court in California to taking part in an extensive computer breach of Sony Pictures Entertainment.
China responded to U.S. claims of alleged involvement in cyberattacks by calling the accusations irresponsible and unprofessional. A defense ministry official attacked attempts to implicate Beijing without proper investigation and irrefutable evidence.
Less than four years ago, American Internet security firm Symantec struck a deal with Chinese infrastructure equipment manufacturer Huawei Technologies, joining forces to develop computer network security products. However, in the wake of increasing cyber security concerns piling up against Huawei, Symantec decided to exit the venture, fearing that it would prevent it from gaining access to U.S. government classified information regarding cyber threats.











![Anonymous Hackers Deface International Police Association Website, “F*CK THE POLICE” [PHOTOS]](https://d.ibtimes.com/en/full/686036/anonymous-hackers-deface-international-police-association-website-fck-police-photos.jpg?w=385&h=257&f=1240826db4239e46d6a4be8785192623)





















