Weak Wi-Fi Router Security Exposed By Flaws In Popular Smart Home Technology

Chances are it’s really easy for just about anyone to infiltrate your home’s wireless Internet router. And the problem is becoming more serious now that consumers are relying on their Wi-Fi networks not just for a Web connection, but to power the Internet of Things, making their locks and household appliances more vulnerable to hackers.
“Internet of Things” is a broad definition for new technology that aims to simplify life: apps and sensors that control home thermostats, door locks, baby monitors, garage door openers and kitchen appliances. But they all rely on home Wi-Fi technnology that's inherently flawed. That, according to a report published Tuesday by cybersecurity company Veracode, means that even if you invest in the best dead-bolt lock on the market, weak security parameters on your Internet-connected garage door opener could make it easy for technologically savvy thieves to break in.
The Veracode report examined six products: the Chamberlain MyQ Internet Gateway, the Chamberlain MyQ Garage, the Ubi voice operated computer, the Wink Relay, the Wink Hub and the SmartThings Hub. Each device is currently for sale on the market and can control mechanical devices (the Wink Relay turning off a home air conditioner, for instance, or the MyQ Garage controlling a garage door).
Researchers followed the out-of-the-box assembly instructions, testing each device on its level of encryption, its password requirements, its SSL certificate validation (which would prevent hackers from intercepting information and using it later). Most fared well, except when it came to requiring strong passwords and protecting against Man in the Middle attacks, when a hacker takes control of the messages sent to and from a device.
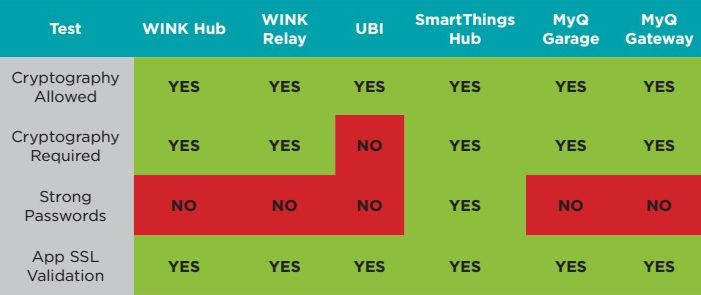
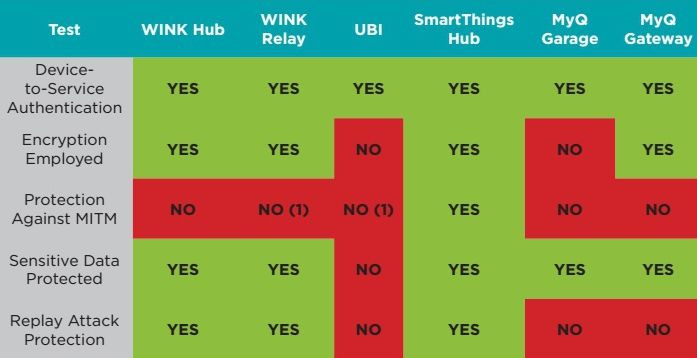
The tests were conducted in January, and by press time Wink had patched its security vulnerabilities. Ubi co-founder Leor Grebler prasied the report, saying his product would be updated “within weeks.” Cory Sorice, head of connected products at Chamberlain, refused to comment on any specifics of the report but said MyQ customers “aren’t challenged” with security.
The report serves as another reminder that most American Internet users are simply lost when it comes to protecting themselves online. The security issues laid out in the report reflect an expectation from IoT companies that the network their product is operating on is safe.
“I don’t think that’s a valid assumption. Wireless routers, especially home ones, are notoriously full of flaws,” said Brandon Creighton, a research strategist at Veracode.
Vulnerabilities most often occur when customers fail to give their network its own name, fail to change the factory password or fail to use a password at all, which is required when customers used WPA-2 security on their router. It's also risky to keep all products on the same network, with Veracode recommending that users compartmentalize their networks in an attempt to separate a possibly infected garage door opener, for example, from the family computer.
“The attack comes down to the security of the local network,” Creighton said. “If there’s any point where someone can access that network chain there can be an attack.”
Most people simply don’t think a neighbor will leech on to their Wi-Fi network, so why use a password? Enough people have used that rationale so that when an IoT company tried to make passwords mandatory, it turned customers off.
“Originally we only supported WPA-2 encryption standards and as a result we had 33 percent of people able to connect, so we had to open up and actually allow for people to connect to it,” said Ubi’s Grebler. “One of the big issues is getting security to work and making it something that’s easy to use.”
© Copyright IBTimes 2024. All rights reserved.




















