Weak MacKeeper Security Exposes At Least 13 Million Users' Sensitive Information: Researcher

Update Dec. 14 12:33 p.m. EST:
MacKeeper posted a statement on its website stating the error had been fixed "within hours of the discovery."
"We will continue to take every possible step to protect the data of our customers from the evolving cyber threats that companies both large and small face on adaily basis," the company stated. "The privacy and security of our clients' information remains our top priority and from the moment we were aware of the access, we immediately took several proactive steps to identify and correct the issue."
Original Story:
Somehow MacKeeper only manages to get worse and worse. The utility software known for inundating users with false advertising appeared to employ bad security measures that could enable attackers to obtain information on millions of users.
That’s the finding from white-hat cybersecurity researcher Chris Vickery, who announced his findings on Reddit late Sunday evening with updates into Monday. Vickery, who previously discovered breaches on Major League Baseball fan sites and in California charter schools, said he would reveal more about how he accessed the data when Zeobit and Kromtech (MacKeeper’s developers) mend the oversight.
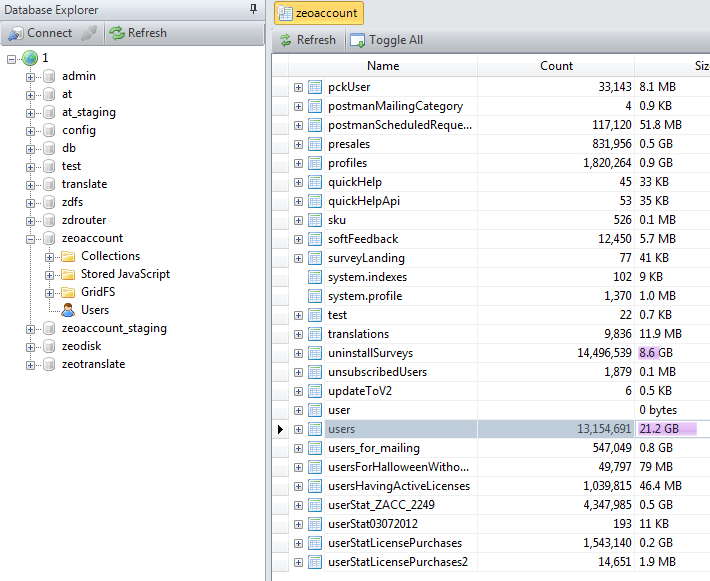
“I have recently downloaded over 13 million sensitive account details related to MacKeeper, Zeobit and/or Kromtech,” Vickery wrote. “It appears to have no respect for the privacy of its users’ data or the integrity of their information.”
MacKeeper did not immediately respond to a request for comment.
MacKeeper promotes itself as a must-have service for Mac users trying to block malicious software or speed up their computer. But it’s commonly associated with spammy advertising methods and automatic downloads, meaning many would-be users’ introduction to MacKeeper consists of their search to delete the software.
Now, after a class-action lawsuit and a promise to stop “scare ads,” Vickery says MacKeeper is failing to protect usernames, email addresses, password hashes, computer names, IP addresses, software licenses, activation codes, hardware details, phone numbers and computer serial numbers.
Vickery has corresponded with the company, he explained on Reddit Monday, but MacKeeper failed to immediately fix the vulnerability.
“I have no malicious intentions for this data,” he wrote. “Right now, the only purpose of me having it is to prove that it was/is available. The company can’t deny the incident if I have the data.”
© Copyright IBTimes 2024. All rights reserved.





















